What do you know about computer privacy and software privacy? Do you have online privacy issues? Do you think you have nothing to hide? Have any internet privacy issues? Think again. You don’t find any good reason for keeping your data private; OK let’s do one thing, how about posting all your bank details, credit card numbers, medical records, text messages, social security numbers, and some of your very private and intimate click on the internet, will that be OK with you?
You might just be looking for online privacy and security news and online privacy and security articles. Saying that you really don’t care about computer privacy and software privacy and actually believing in it, is different. Internet privacy issues exist and it’s important you understand why is online privacy important and it’s important you stay up to date with online privacy and security current events.
If any such data of yours leaked and reached the wrong hands, you will be screwed. Anyone with access to your credit card can steal money, anyone with your medical history can use it against you, anyone with your private photos can easily blackmail you.
The stolen data can easily be posted on the internet, no matter whether you like it or not; we don’t value computer privacy and software privacy until we lose control of our personal data. This is why people have internet privacy issues and why data security and privacy should play an important part in your computer usage.
What Is Privacy to You?
My answer to computer privacy can be different than yours, but our supporting arguments can’t; I believe Privacy (in this case; computer privacy and software privacy) is what sets humans apart from animals, it’s what differentiates you and me from those living under dictatorships and despots. I mean, animals don’t have internet privacy issues and they sure don’t know what data security and privacy is. We often don’t consider privacy, a right, until we need it the most; could be a pull-over at a traffic stop or an arrest at a protest. This kind of mentality applies to computer privacy and software privacy and is why many can develop internet privacy issues. Internet privacy issues are a real thing folks, get good privacy software so you can have computer privacy!
Surveillance challenges both computer privacy as well as software privacy, which is becoming progressively invasive; thanks to the increasing Government eavesdropping which is becoming far more localized and in turn causing internet privacy issues. Rather than blaming Clinton for wiretapping laws, Bush for mass surveillance, and Obama for intelligence expansion, accept the fact that perfect security is just an illusion and take responsibility for your online computer privacy and software privacy. The best way to take care of internet privacy issues is to take your computer privacy into your own hands. Get the best privacy software so you can give yourself the best computer privacy and software privacy to help with your internet privacy issues.
Some professionals like journalists, government workers, and activists – face far more complex threats than citizens like me and you, we only worry about tech companies tracking us to serve up the best ads, or government bulk data collection. But everyone needs to follow a privacy decorum in varying degrees.
Would you mind if most of the apps and services in your PDA start recording your digital footprints? Everybody would. That’s why we need data security and privacy, so we can get over our internet privacy issues and be safe with our computer privacy and software privacy.
So, to avoid all the possible threats that stem from internet privacy issues (discussed below), secure your data with the best privacy software that will help boost your computer privacy and software privacy. Good computer privacy, also means your data security and privacy will come with encryption-friendly apps and practices (discussed below) and turn your data unreadable if hacked or served with a government subpoena.
Did you notice I have used two seemingly inter-related words – Privacy and Security – in different contexts, do you WHY? Because they are not the same, though they seem, sound, and many at times used in a similar fashion.
To clear your understanding, here’s the difference between the two differentiated concepts.
Privacy vs. Security – What is more Important?
Privacy is a situation where you and/or your data is free from observation or accessed by others; who is controlling the accessibility of your data matters. Want to have true privacy? Control who can obtain your information.
Online Privacy (both online computer privacy and online software privacy) is the right that you have on the internet to protect and share personal data with people you want; think about those privacy policies that we instantly check “I agree” before signing up, downloading apps and/or buying products.
Whereas, security is about protection from unwanted third-party intervention; control over what others can access your information.
An inter-relatable definition of privacy vs. security could be;
Privacy is keeping unwanted eyes off of your data, while security is keeping that information private, once it has been collected. Privacy is more about your comfort levels – so, how much info you are comfortable sharing with? This reflects your comfort zone.
Online security is a protection threshold that the internet is offering; it’s how online information is protected. Anyone with skills can access the personal information that you post on the internet; this is you to protect your device/s and so your identity, this is what we called online security.
The laymen understanding could be;
The question – why online computer privacy and security is even needed that badly? – must be surfacing in your naive mind; if yes, then the next few words are for you, others can skip.
Why Online Privacy and Security is Needed?
Consider these; you’ll find the answer yourself!
Lisa is getting divorced; Mia has $700,000 in her bank account; Emmy has intimate pictures in her cell phone; John’s girlfriend is cheating on him; Terry forged his boss’s signature on a legal document.
Have you noticed in every piece of secret I have shared above about these unknown people requires consent; would any of them ever want their secrets to be shared with everyone out there?
Obviously, no one! For everyone, certain things are way private than anything else including, financial standing, Income, Medical records, Personal pictures, and sometimes our darkest secrets.
Imagine you’ve accidentally searched something about kids, the internet soon be considering you that you’re a parent or expecting; the guessing game could reach unknown heights!
That’s why online protection is equally or better to say more important than real-world protection, so don’t take it easy.
Before moving towards potential threats and possible measures to secure your privacy, let’s talk about what an individual user does on the internet; this is somewhat very helpful for hackers to find their prey, actually, our usage is somehow helping them to practice and prosper this profession.
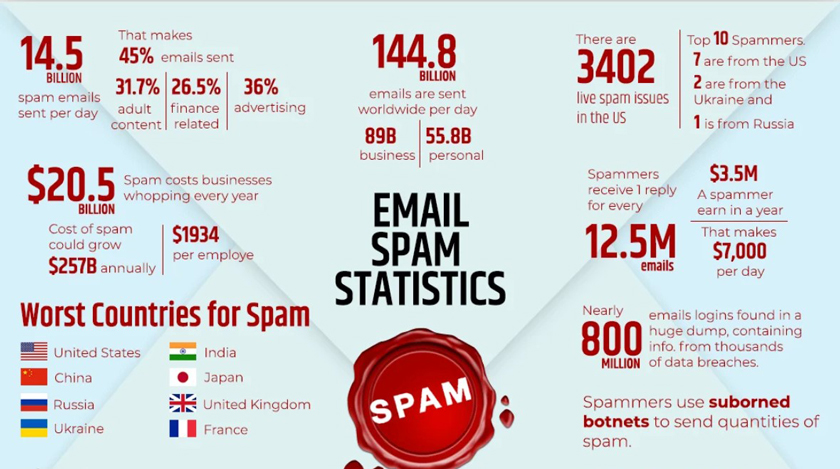
Thanks to Cumulus Media for this compilation.
One minute on the internet
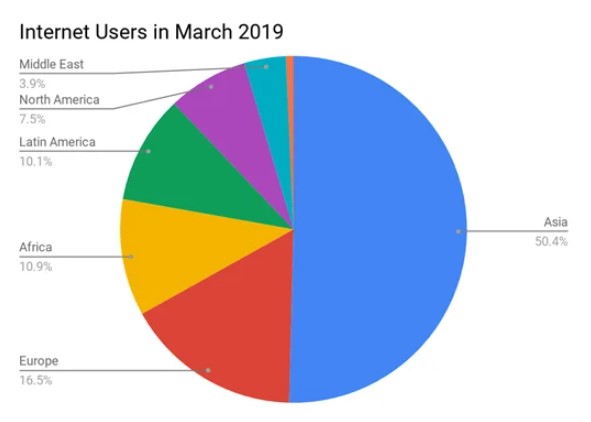
Look at the regional stratification of internet penetration in 2019.
How about if we discuss the global laws which are anti-privacy for online users, before finally proceeding to common threats that can destroy our online security and bypass our data security and privacy?
Shall I?
The Enemies of Online Privacy Across the Globe
These are some of the highly known bills and amendments that are reshaping businesses and individuals, obtaining their information for intended and unintended purposes.
Are you serious about your computer privacy, software privacy, and online freedom? Then you must hate these unprecedented villains of the internet; these developments have fueled VPN usage in the world.
- UK – Browsing history, calls, text messages of the United Kingdom recorded for up to two years; credit goes to the Investigatory Powers Act. The interesting thing is that this private information is available to many government agencies and their global intelligence-sharing partners; this is happening without any warrant.
Let me tell you an interesting fact – according to the General Protection Law; you are legally eligible to request a copy of your all data that an organization holds within 40 calendar days, but have to pay for it.
-
- The USA – With legislation passed in 2017, ISPs can now legally record browsing history and sell the data to advertisers, and third parties; Government mass surveillance also continues, regardless of political influence prevailing in the office. We cannot ignore the abolishment of net neutrality, letting internet providers charge premiums.
- Australia – Australia has also implemented mandatory data retention laws, requiring the collection of calls, text messages, and internet connection data. At worst, Australia is also forcing companies to provide access to encryption, so that government agencies can hack devices and spy on their own citizens. Want more? Online censorship also exists in Australia.
It’s not over, even public-private surveillance cooperation sword also lurking in our cyber world, letting many large tech companies collect huge data through their products and services (detailing below). A big factor as to why many have internet privacy issues.
The good news is that we, users also have something to keep these prying eyes away; use a good VPN with some other privacy tools, to put your data back in your control.
Now, finally, let’s discuss some of the well-known threats that possibly screw up our data, our computer privacy, software privacy and your virtual identity.
Threats, Breaking Our Online Security
Some biggest threats of data security and privacy and internet privacy issues are not only for me or you, it’s also for millions; isn’t strange?
It is, but we have to accept the fact that we are under constant surveillance in several ways that undermine our computer privacy and present us with internet privacy issues, including;
Government Intelligence
We all have heard about Fourteen-eyes surveillance, but never have taken it seriously, same is the case with the ten commandments of the cyber World – Edward Snowden revelations. Be it widespread intelligence-sharing agreements, NSA’s latest programs, India’s new bill, Fourteen-Eyes Alliance, or China’s latest privacy threats; routing your data within either of these, is unsafe. The collected data (both foreign and domestic) is deleted after five years or how long NSA wants.
Using encrypted tools like a proxy, VPN, etc. encrypt your data against govt. surveillance, but don’t forget that encrypted data attract unwanted government attention; your data would stand out.
Browsers and Websites
Cookies, trackers, fingerprints, Etags, key logs, oh my! Web browsers routinely log certain basic information of our internet connection and digital moves. The reported info. to websites help them load faster while there are other factors too.
Your web browser shares IP address, browser, device, display resolution, cookie setting, battery level, plugins, mouse movements and clicks, location, and time zone, with the websites you visit. Not so great if you have internet privacy issues and computer privacy problems.
This combination of the data helps websites to assign your browser, a unique fingerprint; ETags, cookies, fingerprints, etc. are some of the most popular tracking methods used by browsers and websites.
Search Engines
How many times do we google things in a day, scroll up and see how many queries Google handles in a minute? It’s 3.8 billion. Search engines including Google store basic info. of a user; your IP address, time and date, search terms, and a unique identifier stored in cookies (Cookie ID); same case with all the search engines you have visited so far.
The worst case is when search engines hand over the information if requested by a court or government agency; there have been many cases where search histories were successfully used against users in custody, divorce, and criminal cases. Another large problem when it comes to computer privacy, software privacy, and why we have such big internet privacy issues.
Google knows who you are (even your facial and voice recognition), your location (past, present, possible future, mode of transportation and navigations), your communications (contacts, chats, and attachments), likes and dislikes (searches, clicks, online shopping, etc.), and your activities (histories and saved credentials).
Want to have a prove? Recall a Google bug that has exposed 500,000 users’ data.
Isn’t silly to think that you find yourself explaining to a jury that you searched “How to get rid of a body” because you’ve watched Breaking Bad, not because you were planning to kill your ex-girlfriend.
Cloud Storage
No matter whether your cloud storage service encrypts your data or not, privacy isn’t guaranteed! You’d think cloud storage would be a good piece of data security and privacy for your files. But their software privacy can also sometimes cause internet privacy issues.
If they can encrypt so can they decrypt; don’t trust them easily.
Don’t believe in my words? Look closely at the terms and conditions of your trusted cloud storage service provider; there you’ll find that the service provider reserves the right to share your files and data with authorities if asked. Many of them have also cooperated with the NSA.
Remember when we talked about government intelligence-sharing? If the NSA can access your data, it is no longer truly private. That’s why we need data security and privacy, to help curb the internet privacy issues.
Now, let’s find out all the threats that a hacker can pose to an individual user and their computer privacy as well as their software privacy.
To add to our internet privacy issues, a hacker can mess with our computer privacy and software privacy in several ways;
Sends you a malware-loaded email; clicking an email from unnamed and/or unknown accounts can compromise your data. Even a hacker can intercept your important emails if send unencrypted. Malware could be in the form of spyware, that contains malicious malware to fetch your valuable data. Spyware is a self-invited software that installs itself without permission; you’ll find this in the form of pop-ups, email attachments. Spyware could be Trojan, Tracking cookies, Adware, and/or system monitors. And data security and privacy software can have trouble finding them out. Here’s a food for thought;
Attack you with a Phishing attack – it’s a false representation of a legitimate person, institution, or website, asking for personal information via email, call (vishing), SMS (smishing), or any other way of communication. This is another thing that data security and privacy software have trouble stopping, as it relies on the naivety of humans. Find out the intensity of phishing attacks below.
Hack you via unsecured WiFi; we all love free WiFis, but not at the expense of our computer privacy and personal data. You can turn this easy spot into an unbreakable Buckypaper for hackers by simply encrypting your web traffic using tools like VPN.
There could be as many ways/threats as could be, depending on the information trying to hack; sometimes weaker passwords, HTTP websites, keystroke logging also help hackers to intercept our data.
Prevention is better than cure! If we keep our devices protected and keep a check every time we connect to the world of the internet, then hackers can keep their eyes away at least for some time.
How To Tighten Your Online Privacy and Security?
You must be overwhelmed after reading some of the biggest threats to computer privacy, but don’t worry! The protection of your computer privacy is still in your hand; just a few minutes of your life can save you from a disaster later on.
No matter where you are in the world or who you are, there are a bunch of things that you can do to protect your online presence in this turbulent time; follow these 9 principle guidelines and forget being spied or caught.
-
Encryption – Secure emails, messaging, files, hosting…
In a layman’s term, encryption is making readable information into an unreadable character; only a few techies encrypt our data in a way that even they cannot decrypt – End-to-End encryption. So, whenever possible use the service that offers E2EE by default.
To encrypt or to say turn your email into gibberish code – so that only the receiver with the decipher key can read – use Protonmail or Mailvelope if you’re a Gmail user; don’t worry! It has browser extensions to set up quickly.
The only concern with computer privacy and email encryption is that both receiver and sender has the same encryption data security and privacy; isn’t worth especially for sensitive-content emails? Or else your email could be breached like the one that happened recently, in which 773 Million Exposed.
To encrypt your online conversation, use Off-the-Record Messaging; use Pidgin on your Windows, Adium on your Mac OSX, and any other with similar features. Such data security and privacy software is easy to use while keeping your conversation uber-secure and private; send anything but be protected!
The world has more data than anything; it’s our data, so does our responsibility to protect it. No matter you use ZipCloud, CrashPlan, Dropbox, or OneDrive, make sure your data is secure and private. Our experts prefer Sookasa or any other with the same capabilities if you’re using unsecured cloud hosting services; they secure even before you upload your data.
Want to use a protected cloud host for your computer privacy? Use companies like Tresorit and SpiderOak.
-
Password Protected – Use a Password Manager
Password is the first line of defense when it comes to computer privacy, make sure that should be strong, unique and keep-changing; don’t use easily guessed passwords, preferably a combination of letters, symbols, and numbers.
If you keep using one password for all your accounts just because of the fear of forgetting new ones, then hackers will also use the same skills to intrude in your personal info and bypass your computer privacy. So, remain tension-free and do hire a virtual manager to keep your passwords protected; get a password manager like 1Password, LastPass, Dashlane or any other and forget being remembering passwords.
Password managers keep all your passwords in an encrypted database and autofill them when you need them; add their browser extension, or get their mobile version to keep all your app passwords secure.
Some browsers, like Chrome and Firefox, have a built-in password manager, but might be less secure and more vulnerable to security risks than third-party apps.
According to The Guardian, browser auto-fills steal users’ details to conduct phishing attacks; so don’t trust them anymore! It’s better to stick with a third-party password manager, or if you want to track SMS and call to control vishing and smishing, then look for the best option in town.
So, if you want your password to be protected, follow these dos and don’ts to up your computer privacy game;
-
Incognito/Private Browsing – Configure your Browser
As we have discussed earlier, browsers are ignoring our computer privacy and routinely gathering our information in several ways and handing out to those unknown to us.
Even if you don’t want to leave your web browser, then there are some steps that you can take to limit and allow the data to be stored and made available to all the websites you visit.
Regularly clear your DNS cache and cookies to limit the risk of being fingerprinted and tracked on your browser. Some browsers have built-in options to restrict the cookies you accept; find the respective guide and be protected.
Though turning it off or clearing your cache can affect loading times and the overall browsing experience, but you’re protected; you can also limit ETag and other tracking practices in some great browser extensions.
Don’t forget Flash Cookies, which make you easily tracked and don’t get removed even after clearing regular cookies; you have to opt for any reputable programs and/or browser extensions to regularly flush out Flash Cookies.
-
VPN – A One-stop Solution
Don’t want a hassle to deal with so many different data security and privacy software? Want more convenient software privacy? Use a Virtual Private Network and forget being spied from all the unfriendly uninvited evils of the internet – Hackers, Mass surveillance, 14-Eyes Alliance Spies, etc. a VPN with the best encryption (it take billions of years to crack 128-bit encryption with brute force) is perfect for Secrecy and to ensure your connection is anonymous, secure, and private.
To enjoy comprehensive protection online, invest in a best vpn for all devices; setting up a VPN is not only smooth but also protects you from all the scariest threats online in one shot. A VPN combines multiple layers and methods of protection to secure your connection while keeping your online presence anonymous, and private. Not a bad choice for data security and privacy. Or if you’re looking for general software privacy for your internet privacy issues.
A VPN with the anonymous servers encrypt Internet connection from your device to the VPN server, keeping your web traffic away from local and/or international monitoring systems, hackers, Internet service provider, and from surveillance agencies. A VPN masks your physical location and IP address so that you fake your virtual location to browse geo-restricted content more privately.
Keep one thing in mind – a VPN will not protect your web traffic against itself; that’s why it’s important to choose a computer privacy service you trust and does not keep logs of your online sessions.
-
Tor Network – Layers of Protection
Want a gold standard of privacy? Consider using the Tor network. It’s a regular browser with privacy consciousness; if you’re a reporter or activist, Tor is the best for you.
The Tor browser lets your internet traffic anonymously bouncing through multiple voluntarily-run relays (like onions); it does not only hide your internet history but also circumvent state-sanctioned blocks, you can even browse the dark web too.
Use the Tor browser for anything everything, but don’t mind if streaming goes slow.
-
Cloud Storage – But do Encrypt beforehand!
Do you think your cloud storage is encrypted? Then you don’t know your storage closely; pity you for your blind trust! Look closely at the terms and conditions of your or any other popular cloud storage service/s you will get to know.
If you are going to rely on cloud storage for your files, choose the one that can automatically encrypt files before uploading to the cloud so you can get the best out of computer privacy. Although providers have the decrypting keys, this does not mean that we should give up the idea of cloud storage; rather go for manual encryption before uploading data to your cloud storage service, in that case, the key to decode will only be with you.
Click on these links to read up more on our recommended safest cloud storage and cheapest cloud storage.
-
Anti-Malware and Firewall – A Single Virus Can Damage Your Device
Yes, you heard it right! A single virus can do more damage than one can think of; protecting from malware is easier than fixing the damage already done, by using anti-malware data security and privacy software. So, do scan your computer regularly to find and get alerts for suspicious or harmful files.
Other than anti-malware software for your data security and privacy, firewalls are also crucial that monitor the traffic coming to and from your computer; make sure that no unauthorized data is downloaded or sent. Set the firewall to block certain traffic automatically and let other web traffic is to let through.
A one-way firewall protects your computer from malware and a two-way firewall protects your privacy too; not only stops unwanted traffic but also prevents programs from accessing the internet without permission.
Click on this link to read up more on cheap antivirus and best malware protection for windows and android.
-
HTTPS or HTTP – Go with the Former
Secure websites use HTTPS encryption for data security and privacy protection that are being exchanged between you and the server.
HTTPS is the extended version of HTTP and is also known as HTTP over TLS (Transport Layer Security); HTTP over SSL (Secure Sockets Layer) is TLS’s predecessor.
You can easily check whether a website is HTTPS protected by looking at the URL; sometimes you will also be notified if you are visiting a non-secure server, which is under the control of your ISP or any third-party spying eyes.
-
Two-Factor Authentication – Secure your Logins
Two-factor authentication is available with popular sites and services that prompt you for a password followed by a short security code that is sent to the synced phone. Like while logging into your Gmail account, you’ll receive a text message with a shortcode from Google, type that before you could access your account on any new machine.
I know this is way annoying! Truth be told, once you’ve configured two-factor authentication, it takes just an extra 15-20 seconds to log in, but protection is obvious.
I know it’s quite much, but it’s a matter of our online security and privacy; our online presence reflects our true being, and it needs to be protected.
Our experts invest hours in making our online presence as secure as possible; one of our experts have recommended some of the tips with us to limit the increasing vulnerabilities from being exposed.
Allow me to share with you; don’t worry! They are a few and easy!
- Minimize your social media use
- Be careful about the permissions to apps
- Keep updating your apps, devices, and OS
- Use the web version of Facebook instead of the app
- Be cautious with IoT devices
- Avoid public WiFis
- Download files from trusted sources
- Use free open source software and privacy software
- Use secure payment methods
- Try to avoid fingerprint
- Reduce your digital footprint
- Delete accounts you are not using
Online Security and Privacy in the Business World
Our security and computer privacy is now secured, but what about the businesses, how startups, and million dollars organizations can save themselves from the biggest data breaches?
Here is the answer!
Before proceeding, let me tell you some real-life stories about computer privacy; if you think a cybercriminal can never challenge your entrepreneurship skills and challenge your software privacy and data security and privacy, then these stories are for you to haunt back.
These data breaches will tell you how vulnerable the business world and its computer privacy have become; again thanks to hackers.
The security and computer privacy of your business is positively proportional to your customers’ privacy, brand’s goodwill, and growth of the business; so once your business is secure, the rest of things will adjust themselves.
To make it simple for our business friends, who are damn busy with their latest venture/s, we are throwing 9 questions across; ask yourself to find the loophole/s and then solve in the respective capacity.
Ask These Questions To Keep Your Business Secure From any Data Breach
- Are you and your employees password-protected? If no, then immediately get a password manager and remain protected.
- Are you religious about 2FA Two factor Authentication? Don’t say NO, it’s imperative!
- Do your employees and/or your smartphone is the work phone too? Try to keep them separate.
- Has your data been backed up already? Don’t take a chance, get a backup ready!
- Are your business devices and connections protected and encrypted? If not yet, then waste no more time and get connected with a business VPN and antivirus; update in case you have them already.
- Are your employees restricted to their area of the domain? If yes, then it’s perfectly fine otherwise, restrict them with ‘Admin Rights Only’ and give only to those who need it.
- Are your employees trained enough? If no, then invest some bucks into online security and make your team ready to face cyber threats.
- Is your business data and customers’ info. encrypted? This is what where business credibility can be challenged, so get your data encrypted with tools like VPN.
- Is your business website adequately protected? If no, then be prepared to host a breach, as most attacks happen on WordPress; you can still secure your website by staying up-to-date on WP, keeping backups, installing updates, and free from dodgy plugins.
Before leaving you back in the World of hackers and cyber surveillance, let me remind you all the basic tips and tricks regarding data security and privacy one more time; we are sure you won’t forget this privacy checklist and leave your data security and privacy vulnerable.
- Check your public social media profiles only for personal content.
- Tweak the privacy settings across all your accounts.
- Don’t settle for less than a strong, unique password for your accounts.
- Keep reviewing emails safety practices and be alert to phishing hacks.
- Use end-to-end encrypted services – VPN.
- Update your security settings and turn two-factor authentication on.
- Install software updates for all apps and operating systems.
- Install the HTTPS browser extension.
- Make Tor, your all-time friend.
Do Whatever You Want, But be on the Safe Side!
We hope this roller-coaster ride of breaches and measures might have disturbed the chemical of your brain but must have cleared one thing, that there’s no superman other than you who can control the increasing threats of the cyber world. The sooner you take your computer privacy and online privacy seriously, the quicker these musketeers would go away from you and your business; take positions and get your armors ready.
Here at VPNveteran, we use our 360-degree lens and review the changes and challenges surfacing in the cyber world; and then share our biased opinions with our readers.
What is safe for computer privacy now may be disastrous tomorrow, new threats are emerging that are constantly changing the opinions surrounding tech. Thanks to our experts to keep updating this guide as the changes occur.
This guide is the result of our experts’ extensive efforts and dedication; so, don’t forget to give your feedback and in case we’ve missed something, do point us in the comment section below.